Which of the Following Use the Csma/cd Access Method
CSMACD detects whether the channel is free or busy before transmitting data so that it can avoid collision whereas ALOHA cannot detect before transmitting and thus multiple stations can transmit data at the same time thereby. The servers called.

Csma Cd Protocol Ieee802 3 Youtube
DSTP Data Space Transfer Protocol is a protocol that is used to index and retrieve data from a number of database s file s and other data structures using a key that can find all the related data about a particular object across all of the data.
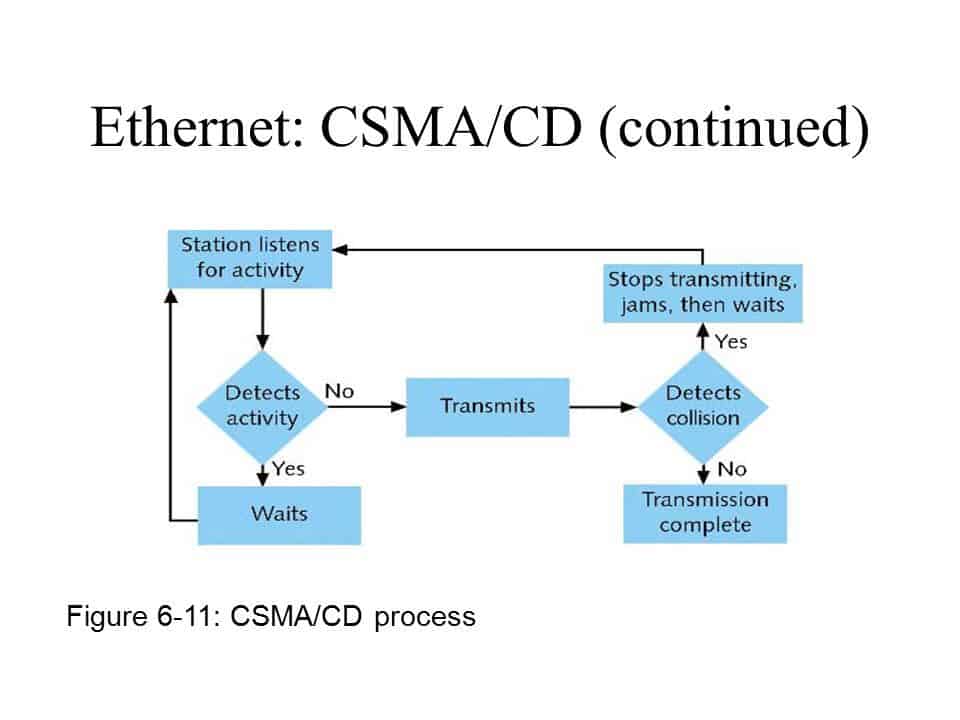
. In that case the bus is free both nodes transmit their dominant start bit Multiple Access. The CSMACD protocol works with a medium access control layer. The main difference between ALOHA and CSMACD is that ALOHA does not possess the feature of carrier sensing like CSMACD.
You can even use six different Microsoft Teams accounts simultaneously if thats what you want to do. Make sure to follow all the steps in the order they have been listed. The data is typically distributed among a number of server s in a network.
The bus access method is CSMACDAMP Carrier Sense Multiple Access with Collision Detection and Arbitration on Message Priority. The data link layer provides the functional and procedural means to transfer data between network entities and may also provide the means to detect. If any collision is detected in the CSMACD the station sends a jam stop.
If not upgrade from the home version first. 105ºC is supported only in the 64-QFN with an external voltage regulator internal regulator must be disabled and 25V typ Ethernet magnetics. - Ability to use low cost 25MHz crystal for reduced BOM Packaging - Pb-free RoHS compliant 64-pin QFN or 64-pin TQFP-EP Available in commercial industrial and extended industrial temp.
Therefore it first senses the shared channel before broadcasting the frames and if the channel is idle it transmits a frame to check whether the transmission was successful. CSMA is a network access method used on shared network topologies such as Ethernet to control access to the network. This feature makes it easy to connect one PC to another for desktop support and file access.
Every bus node reads back bit by bit from the bus during. Cryptography in Network Security is a method of exchanging data in a particular form. Create a New PC Account and Switch Between Users.
Carrier Sensed Multiple Access CSMA. The resultant bit is then. At the Sender side the data is divided into equal subunits of n bit length by the checksum generator.
This sum is of n bits. If the frame is successfully received the station sends another frame. In symmetric key cryptography sender and receiver use.
Devices attached to the network cable listen carrier sense before transmitting. The following information describes the operation of Modbus TCPIP as it relates to Acromag Series 900EN-40xx IO modules. MA Multiple Access indicates that many devices can connect to and.
According to this algorithm both network nodes wait until the bus is free Carrier Sense. Also this method works only on Windows. This workaround requires a bit more time to complete and consists of 14 steps.
Since this feature is disabled by default the first step is to enable RDP to use it. IN CSMACD Access Method every host has equal access to the medium and can place data on the wire when the wire is free from network traffic. This bit is generally of 16-bit length.
The data link layer or layer 2 is the second layer of the seven-layer OSI model of computer networkingThis layer is the protocol layer that transfers data between nodes on a network segment across the physical layer. This method makes the use of Checksum Generator on Sender side and Checksum Checker on Receiver side. Remote Desktop Protocol has been a feature of Windows since XP Pro.
These subunits are then added together using ones complement method. An Access Method determines how a host will place data on the medium. If the channel is in use devices wait before transmitting.
First confirm that you have Windows 10 Pro. When a host wants to place data on the wire it will check the wire to find whether another host is already using the medium. Cryptography Techniques- Symmetric key cryptography and Asymmetric key cryptography.

What Is Csma Cd Csma With Collision Detection
No comments for "Which of the Following Use the Csma/cd Access Method"
Post a Comment